Cybersecurity Career Paths - Incident Response, SOC
I will be doing a deep dive on Incident response (IR for short) and Security Operations Center (SOC for short). I have grouped these together as a lot of the times they are used interchangeably. This will be part 2 of a 4 part series around cybersecurity career paths.
I have experience working in these areas as in most of my time in Cybersecurity I have conducted IR and in my last job, we operated in a more traditional SOC environment. What this means is there are tiers for Analysts.
Tier 1, Tier 2, and Tier 3
Tier 1
In this role, you are triaging alerts that come in. This could be phishing emails, laptop related events, server related events, malware, etc. In this role, you would give an alert a first pass, assign its priority and pass it onto the Tier 2/Tier 3. Your job would be to not let something go untriaged
Tier 2
In this role, you are taking over the handoffs from the Tier 1. Alerts that need more analysis and follow up. Your job would be to ensure all alerts are closed or escalated(if needed)
Tier 3
In this role, you will be handling escalations only. (Keep in mind, sometimes Tier 2 and 3 are one in the same) Think larger scale incidents and cases where remediation will be necessary. Your job here would be to be the lead for the team. Handling any escalations brought upward and guiding the other analysts.
The above is for a traditional SOC. There can be shifts, where there is a day shift, a swing shift and a night shift.
What has been a trend (especially in tech companies) is a more flat approach. Where there is a lead, and the rest of the team all handles the same body of work. This means initial triage, escalations, to closing out incidents. This is usually operated in a rotation, where one analyst is on point for a week (or some other period of time) and they handle all alerts and incidents for that time. Of course, pulling in teammates or their lead whenever necessary. This is what I have seen in the private sector, and what I operate out of.
Incident Response
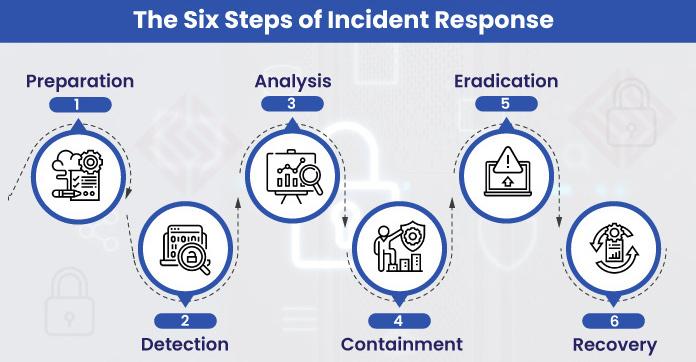
Steps of Incident Response lifecycle
Incident response is sometimes used interchangeably with SOC as it can be conducted by the same team. Although it can be a team on its own. In this area of Security, operating under pressure and being able to coordinate moving parts is crucial.
You can think of this area of Cybersecurity as paramedic work, often working in adverse circumstances but needing to execute the task at hand. When you read about a breach and all the work that was done in recovery of it, you can bet the Incident Response team was behind the scenes coordinating the efforts to remediate the situation. You can think of this last piece of the job as Traffic Control, needing to be able to coordinate the moving parts and keep order in an otherwise stressful situation. Someone could make an entire career in Incident Response as it is always in demand and is a skill sought after.
For more details on the Incident Handling lifecycle see
https://www.sans.org/media/score/504-incident-response-cycle.pdf
For resources to learn even more see
https://github.com/meirwah/awesome-incident-response
Hope this was helpful in understanding the career path and domain of Incident Response.
